The massive adoption of cloud solutions is profoundly transforming the corporate IT landscape. This outsourcing offers flexibility, scalability and often cost reduction, but raises major challenges in terms of data protection.
The General Data Protection Regulation imposes a strict framework that every organization must comply with, including when it delegates the processing of its data to external service providers.
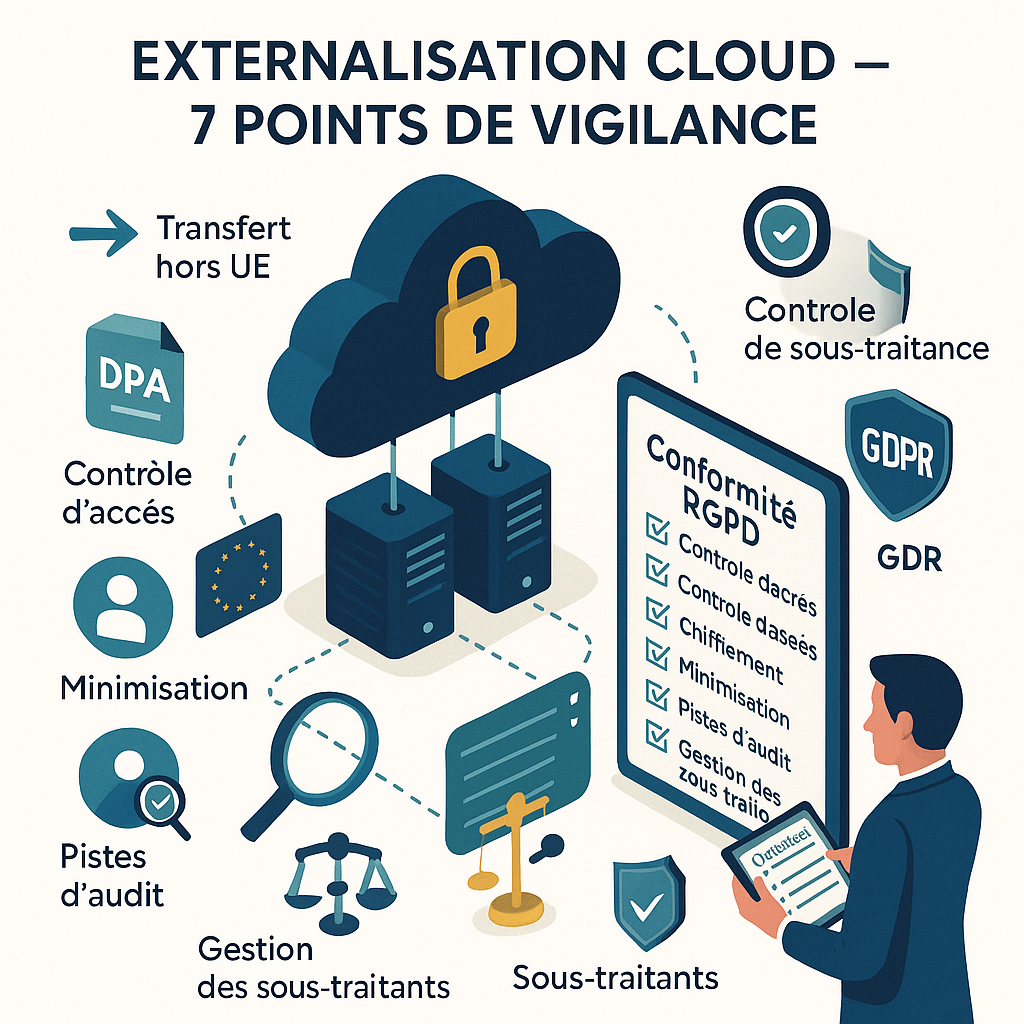
Between technical constraints and legal obligations, navigating the waters of cloud computing while maintaining RGPD compliance requires particular vigilance on several critical points.
If you're looking for an IT outsourcing lawyer, contact me!
The legal status of players: an essential prerequisite
In the RGPD ecosystem, the precise legal qualification of the various players is the cornerstone of any compliance approach. This preliminary step determines everyone's responsibilities and obligations, with significant legal consequences.
In acloud outsourcing relationship, the company that defines the purposes and means of processing retains its status as data controller. This qualification implies overall responsibility vis-à-vis data subjects and supervisory authorities, even when the processing is actually carried out by a third party. This responsibility cannot be contractually delegated, and persists throughout the entire subcontracting chain.
The cloud service provider generally qualifies as a processor within the meaning of the RGPD. This qualification imposes specific obligations on it, including acting only on documented instructions from the controller, implementing appropriate security measures, and assisting the controller in exercising the rights of data subjects.
Complexity increases when the value chain involves several players: infrastructure providers (IaaS), platform providers (PaaS), application providers (SaaS), and integrators. In these configurations, each player must be precisely qualified, and his or her obligations clearly defined. Joint responsibility, provided for in Article 26 of the RGPD, may also apply when several entities jointly determine the purposes and means of processing.
This legal qualification must be formalized in contractual documents and reviewed periodically, particularly when services or technical architecture evolve.
Contractual framework: transforming legal obligations into enforceable commitments
The GDPR has considerably strengthened the requirements for contractual relationships between data controllers and processors. Article 28 of the Regulation now imposes a mandatory minimum content for any subcontracting contract involving personal data.
In the context ofcloud outsourcing, these contractual provisions are of particular importance. The standard contracts offered by major cloud providers are often insufficient to meet these requirements, necessitating specific negotiations or endorsements dedicated to data protection.
In particular, the contract must specify the object and duration of the processing, its nature and purpose, the type of data involved and the categories of people concerned. In addition to these descriptive elements, the contract must impose specific obligations on the cloud provider:
- Process data only on the basis of documented instructions from the controller
- Guarantee the confidentiality of persons authorized to process data
- Implement appropriate technical and organizational security measures
- Respecting the conditions for hiring a subsequent subcontractor
- Help the manager fulfill his or her obligation to respond to requests from data subjects
- Assist the manager in fulfilling his security and data breach obligations
- Delete or restore all data on completion of services
- Provide all the information needed to demonstrate compliance with obligations
These obligations must be translated into concrete commitments, adapted to the technical and operational reality of the cloud service concerned. For example, the obligation to provide assistance in the event of a data breach must specify notification deadlines, the format of information to be provided, and coordination procedures between teams.
To navigate these contractual complexities and secure your relationships with cloud providers, consulting an IT outsourcing lawyer will help you establish a contractual framework that complies with regulatory requirements while preserving your company's operational agility.
Data localization: a strategic issue for international data transfers
The question of the geographical location of data is one of the major challenges forcloud outsourcing in the context of the RGPD. The regulation imposes strict conditions for data transfers to third countries, i.e. outside the European Economic Area (EEA).
These conditions were tightened considerably following the "Schrems II" ruling by the Court of Justice of the European Union in July 2020, invalidating the Privacy Shield, which provided a framework for transfers to the United States. This ruling also tightened requirements on the use of standard contractual clauses, now imposing an in-depth analysis of the level of protection offered by the recipient country.
In this context, several strategies can be considered forcloud outsourcing:
Give preference to sovereign cloud solutions whose infrastructure is entirely located in the EEA and operated by entities that are legally independent of any extraterritorial legislation. This approach offers the greatest legal certainty, but may limit technical options and generate additional costs.
Opt for regional offers from major international suppliers, with contractual guarantees of data localization in the EEA. This intermediate approach reduces the risks associated with transfers, but does not totally eliminate them, particularly in view of potential access for maintenance or support purposes.
If transfers outside the EEA are unavoidable, put in place a robust compliance framework including standard contractual clauses, supplemented by additional technical and organizational measures. These measures may include data encryption with exclusive key control by the client company, systematic pseudonymization, or strict access control mechanisms.
Whatever approach is adopted, a precise mapping of data flows and a documented risk assessment are essential. This analysis must be regularly updated to take account of legal and regulatory developments in this particularly dynamic field.
Security and confidentiality: shared responsibility in the cloud
Data security is a fundamental obligation for both the controller and the processor under the RGPD. This obligation translates into the implementation of "appropriate technical and organizational measures" to guarantee a level of security appropriate to the risks.
In acloud outsourcing environment, this responsibility is necessarily shared according to a model that varies according to the type of service involved (IaaS, PaaS or SaaS). This shared responsibility model must be clearly defined and understood by both parties.
For infrastructure solutions (IaaS), the cloud provider generally ensures the physical security of datacenters, network and hypervisor security, while the customer remains responsible for the security of operating systems, applications and data. At the other end of the spectrum, for SaaS applications, the provider assumes a much greater share of responsibility, with the customer concentrating primarily on access management and service configuration.
This division of responsibilities must be formalized contractually, with precise commitments on both sides. In particular, the contract must specify :
- Security measures implemented by the cloud provider (encryption, access controls, monitoring, backup, etc.).
- Compliance with security certifications and standards (ISO 27001, SOC 2, etc.)
- Security incident notification and management processes
- Audit and compliance verification procedures
Beyond the contractual aspects, operational security governance must be put in place, with periodic reviews of implemented measures and active monitoring of potential vulnerabilities. The training and awareness-raising of internal users is also an essential part of this overall approach.
Managing subsequent subcontractors: controlling the processing chain
Modern cloud ecosystems are often based on complex chains of subcontracting, with the main provider itself calling on multiple service providers for different aspects of the service (infrastructure, maintenance, support, etc.). This operational reality poses a major challenge in terms of RGPD compliance, with Article 28 imposing a strict framework for further subcontracting.
The data controller must give prior authorization, either specific or general, for the engagement of subsequent subcontractors. In the case of general authorization, which is common in standard cloud contracts, the supplier must inform the customer of any planned changes, and give him the opportunity to object.
In addition to this procedural requirement, the main processor must pass on to its own subcontractors the same obligations as those imposed by the controller. The aim of this contractual cascade is to guarantee a uniform level of protection throughout the value chain.
In practice, managing subsequent subcontractors as part ofcloud outsourcing requires :
Full visibility of the cloud provider's partner ecosystem, ideally through a regularly updated list accessible to the customer. This list should specify the role of each subcontractor and the data to which they potentially have access.
A formalized process for notifying changes, with a reasonable timeframe allowing the customer to assess the implications and, if necessary, object to the introduction of a new subcontractor presenting excessive risks.
Contractual guarantees concerning the diligence carried out by the main supplier to ensure the compliance of its own subcontractors, ideally backed up by evidence (audit reports, certifications, etc.).
Particular attention must be paid to subcontractors located outside the EEA, who combine the issues of further subcontracting and international transfers, thus multiplying compliance requirements.
Exercising data subject rights: streamlining processes in the cloud
The RGPD grants data subjects extensive rights over their personal data: right of access, rectification, erasure, limitation, portability, and opposition. The effective exercise of these rights is a central element of compliance, requiring effective collaboration between the data controller and its processors.
In acloud outsourcing context, this collaboration can come up against technical and operational obstacles. Complex architectures, the dispersal of data across different platforms, or replication and backup mechanisms can make it difficult to identify and manipulate the data of a specific individual.
To meet this challenge, several complementary approaches can be implemented:
Contractually define the respective responsibilities of the customer and the cloud provider with regard to the exercise of rights, specifying support deadlines, data formats and communication channels to be used.
Give preference to cloud solutions offering native rights management functionalities: administration interfaces for locating and extracting an individual's data, APIs dedicated to portability, erasure mechanisms guaranteeing complete deletion of data, including in backup systems.
Set up detailed operating procedures for each type of request, with templates for requests to be sent to the cloud provider and tracking mechanisms to ensure legal deadlines are met.
Systematically document requests received and actions taken, so as to be able to demonstrate to the supervisory authorities compliance with obligations in terms of data subject rights.
The ability to exercise these rights effectively needs to be assessed as early as the cloud provider selection phase, and then tested regularly throughout the contractual relationship. Simulation exercises can be particularly useful in identifying and correcting any shortcomings in these critical processes.
Data breaches and crisis management: orchestrating a coordinated response
Security incidents in the cloud environment are a reality that every organization needs to prepare for. The RGPD imposes strict data breach notification obligations, with a 72-hour deadline for informing the supervisory authority and, in some cases, an obligation to inform data subjects directly.
In acloud outsourcing context, effective management of these situations requires close coordination between customer and supplier. The contract must precisely define the responsibilities of each party, including :
The obligation for the supplier to notify the customer of any data breach within a timeframe compatible with the latter's legal obligations (generally 24 to 48 hours maximum).
The level of detail of the information to be provided at the time of notification: nature of the violation, categories and approximate number of people concerned, likely consequences, measures taken or proposed to remedy the situation.
Escalation procedures and dedicated contact points for incident management, with secure communication channels available 24/7.
The division of responsibilities for the technical investigation, evidence gathering and forensic analysis of the incident.
Beyond these contractual aspects, operational preparation is essential to react effectively in a crisis situation. Simulation exercises involving customer and supplier teams help to test procedures and identify areas for improvement. Notification templates pre-validated by legal departments can also help reduce response times.
Systematic documentation of all incidents, even minor ones, is a good practice that enables us to continually improve our prevention and detection systems. This documentation may also prove invaluable in the event of a subsequent inspection by the data protection authority.
Reversibility and portability: anticipating the end of the cloud relationship
Technological dependency is one of the major risks ofcloud outsourcing. Without clearly defined mechanisms for reversibility and portability, a company can find itself a "prisoner" of its supplier, unable to migrate to an alternative solution without significantly disrupting its business.
This issue takes on a particular dimension with regard to the RGPD, which enshrines a right to portability of personal data and imposes strict obligations concerning the return or deletion of data at the end of a contract.
To reduce this risk, several complementary approaches can be considered:
Favoring solutions based on open standards and widely adopted exchange formats, thus reducing technological dependency and facilitating future migrations.
Negotiate detailed contractual clauses concerning reversibility, specifying in particular the format of the data returned, the associated metadata, the technical documentation provided, and the assistance offered by the outgoing service provider.
Define a sufficient transition period (usually 3 to 12 months) during which the cloud provider continues to provide service while supporting the migration to the new solution.
Develop and maintain a technical architecture that favors vendor independence, for example by limiting the use of proprietary services that are difficult to transpose, or by maintaining abstraction between business applications and the underlying cloud services.
Periodic data recovery tests can validate the effectiveness of reversibility mechanisms, and identify any gaps before they become critical. These tests are part of a broader approach to managing the risks associated withIT outsourcing.
Towards a strategic approach to cloud compliance
RGPD compliance in acloud outsourcing environment cannot be reduced to a simple list of checks to be carried out or clauses to be included in contracts. It requires a strategic approach, integrated into the company's overall governance and aligned with its business objectives.
This strategic approach is based on several guiding principles:
The integration of compliance requirements right from the design phase of cloud projects (privacy by design), making it possible to anticipate problems rather than trying to solve them after the fact.
The adoption of clear data governance, defining responsibilities at all levels of the organization and ensuring consistent management of the lifecycle of personal data, from collection to deletion.
The development of a culture of data protection within the company, through training and awareness programs tailored to different audiences (technical teams, business lines, management).
The implementation of an ongoing assessment of risks linked to the processing of personal data, with particular attention to technological and regulatory developments likely to impact compliance.
Close collaboration between the various functions involved: IT, legal, security, business and, of course, the Data Protection Officer (DPO), whose role is central to this system.
This strategic approach not only ensures compliance, but also transforms regulatory constraints into opportunities to improve internal processes and strengthen customer and partner confidence.
Turning regulatory constraints into competitive advantage
Far from being a mere legal obligation, RGPD compliance in the context ofcloud outsourcing can be a real lever for differentiation and value creation. Companies that take a proactive approach to personal data protection enjoy multiple benefits:
Strengthen the trust of customers and partners, who are particularly sensitive to the ethical and responsible management of their data in a context of growing awareness of privacy issues.
Improved data quality and governance, contributing to operational efficiency and the relevance of decision-support analyses.
Reduced operational, legal and reputational risks linked to security incidents and data breaches, with potentially significant financial impacts.
Greater agility in the face of regulatory changes, with the adoption of good data protection practices making it easier to adapt to the new legal requirements that are bound to emerge in this dynamic field. To realize these benefits, RGPD compliance must be integrated into the company's overall strategy and taken to the highest level of the organization. It requires an initial investment in terms of human, technical and financial resources, but ultimately constitutes a major competitive advantage in a digital environment where trust is becoming as precious a currency as the data itself.